Exein Runtime
The Exein runtime agent operates in the background to analyse system behaviour, apply security policies and emit events to the Exein managed platform.
Pulsar
Pulsar is a powerful, blazing fast security observability framework designed specifically to address the challenges of embedded security of Linux devices.
Runtime security for the IoT
Pulsar is a highly modular, event-based runtime security framework. Designed for IoT and edge computing, Pulsar is optimized for performance, runtime cost, and edge security.
Blazing Fast
Pulsar's core architecture is written entirely in Rust, a modern and secure language that allows for extreme performance even in constrained environments.
Highly Modular
Pulsar modular design makes it easy to adapt the core architecture to diverse use cases. You can create and load modules that collect the events you need and customize all the security policies you want to enforce.
Powered by eBPF
Pulsar uses the latest eBPF technology to trace and collect system activity information directly from the kernel. eBPF is safer and faster than legacy solutions built on kernel modules, and requires no kernel patching.
Pulsar functionalities
- Track filesystem activity and block access to files with path based rules.
- Monitor all network related events, and scan for suspicious connections.
- Detect any process execution and behavior changes.
- Write your own security policies easily in a human readable format.
Running Pulsar
Configure Exein Runtime
Modify the file /var/lib/pulsar/pulsar.ini according to your needs.
# registration_token=<account_token> account token assigned by Exein.
Start Pulsar agent
To start Pulsar, run the follow command:
# pulsar-enterprise-exec pulsard&
Registering with the platform
On the first launch of the Pulsar agent, the registration process triggers automatically with the agent connecting to the platform using its unique registration token. After successful registration, a unique certificate pair is provided to the agent to store on disk. On subsequent launches of the Pulsar agent, the certificate pair will already be available and will automatically connect to the platform with no additional intervention required.
Testing
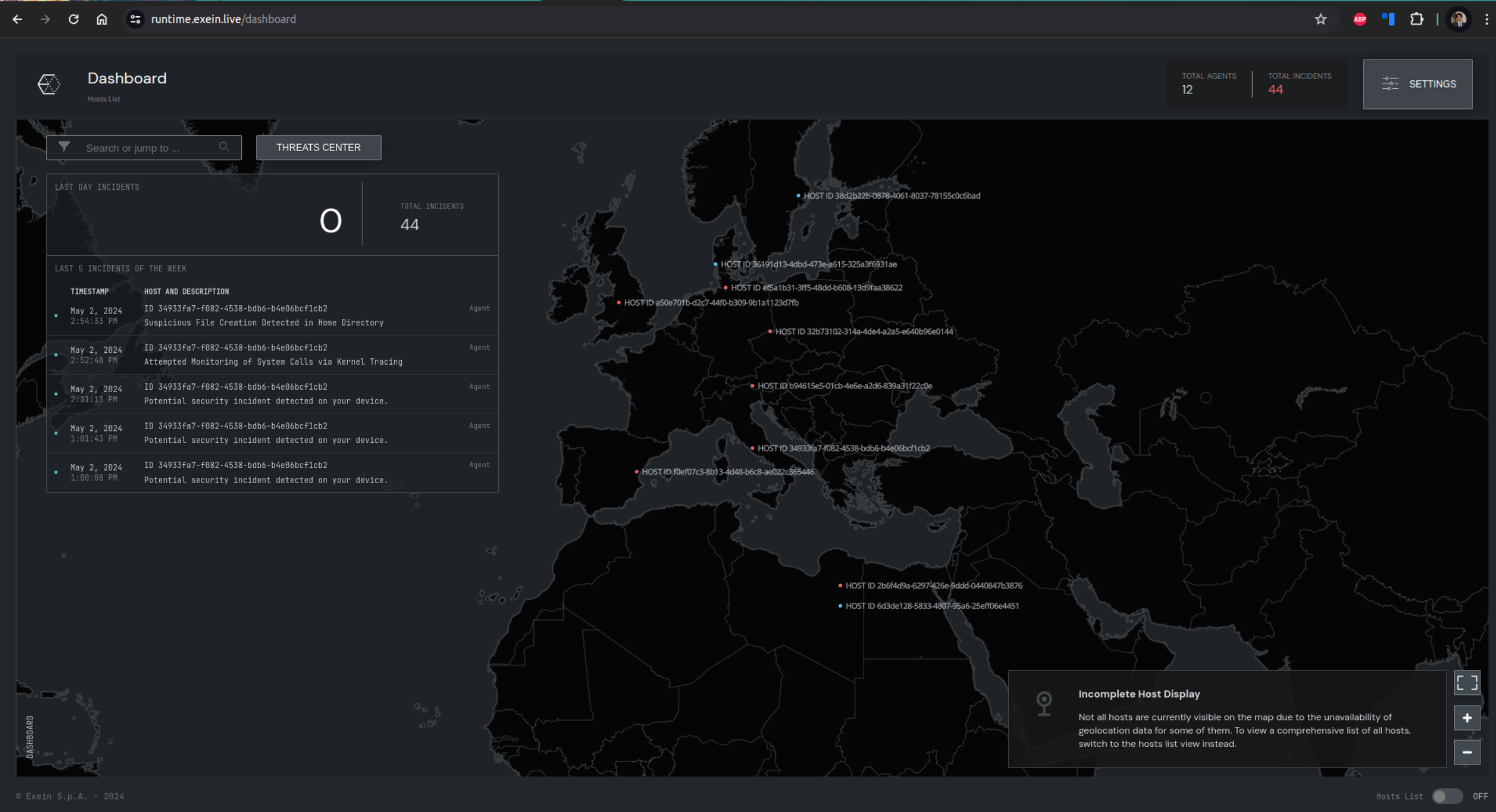
Accessing the Exein Runtime dashboard (https://runtime.exein.live/) with the provided credentials will allow you to login and monitor the status of your agent. There are threescenarios that you may encounter.
- There is an agent listed and is in an Active state. This means that the registration was successful and the agent has begun sending heartbeats and events to the platform.
- There is an agent listed and is in a Pending state. This means that the agent has been pre-generated for you, however we have not received a registration request yet from the agent.
- There is no agent. This means that the agent has not been pre-generated for you and we have not received a registration request from the agent yet.
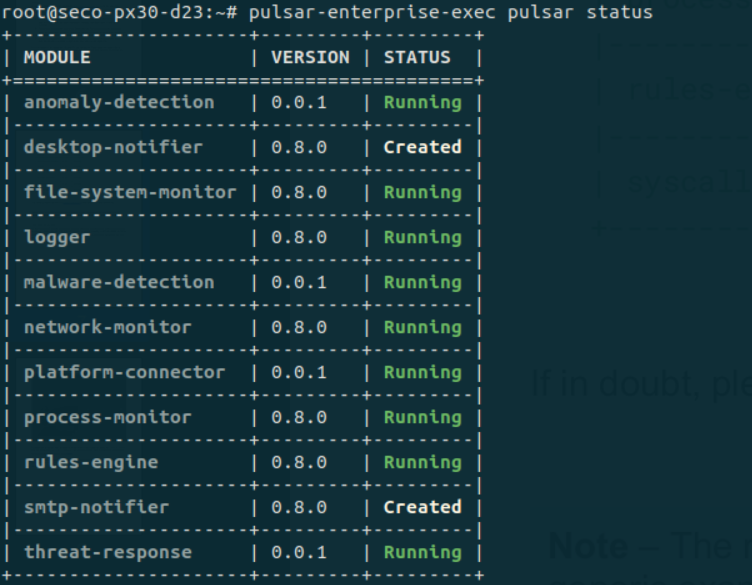
For Linux agents, for scenarios (2) and (3), examining the Pulsar daemon logs will help provide context as to why the registration is failing. These can be observed by running the following command.
# pulsar-enterprise-exec pulsar status
Triggering an Incident
To test the Exein Runtime capabilities, you can manually perform some potentially malicious actions on the host device. If the Pulsar daemon is up and running, it will spot these activities and generate an incident that you can inspect inside the Exein Runtime platform in order to gain more insight into what happened on the device.For example, a simple way to trigger a threat event is by trying to access the /etc/shadow with the command cat /etc/shadow run.